It is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will typically direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website, however, is bogus and will capture and steal any information the user enters on the page.
Phishing, also referred to as brand spoofing or carding, is a variation on “fishing,” the idea being that bait is thrown out with the hopes that while most will ignore the bait, some will be tempted into biting.
Here is an example of what a phishing scam in an email message might look like.
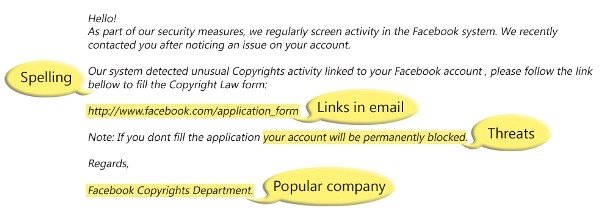
A phishing scam typically operates as follows:
- The victim receives an official-looking email message purporting to come from a trusted source, such as an online banking site, PayPal, eBay, or other service where money is exchanged, moved, or managed.
- The email tells the user that his or her account needs updating immediately or will be suspended within a certain number of days.
- The email contains a URL (link) and instructs the user to click on the link to access the account and update the information. The link text appears as though it will take the user to the expected site. However, the link is actually a link to the attacker’s site, which is made to look exactly like the site the user expects to see.
- At the spoofed site, the user enters his or her credentials (ID and password) and clicks Submit.
- The site returns an innocuous message, such as “We’re sorry—we’re unable to process your transaction at this time,” and the user is none the wiser.
- At this point, the victim’s credentials are stored on the attacker’s site or sent via email to the perpetrator, where they can be used to log in to the real banking or exchange site and empty the account before the user knows what happened.
Protect yourself by taking the following steps
- Look for telltale signs of fraud: Instead of addressing you by name, a phishing email addresses you as “User” or by your email address; a legitimate message from legitimate companies uses your name as they know it.
- Do not click on links embedded in unsolicited finance-related email messages. A link might look legitimate, but when you click on it, you could be redirected to the site of a phisher. If you believe that your account is in jeopardy, type in the known URL of the site in a new browser window and look for messages from the provider after you’re logged in.
- Check with your provider for messages related to phishing scams that the company is aware of. Your bank or other financial services provider wants to make sure you don’t fall victim and will often take significant measures to educate users on how to prevent problems.
A phishing toolkit is a set of scripts that allows an attacker to automatically create websites that spoof the legitimate websites of different brands, including the images and logos associated with those brands. The scripts also help to generate corresponding phishing email messages. Phishing toolkits are developed by groups or individuals who sell the kits in the underground economy. There are two types of phishing toolkits:
- Domain-based phishing toolkits that require the phisher to own and register a unique domain, such as “devil.com” and host it somewhere like a bot network or on an ISP.
- Defacement-based phishing toolkits that do not require the registration of domains or DNS servers so they are easier to set up. Defacement-based phishing toolkits require a phisher to compromise existing web pages, after which the phisher can simply upload the page of the spoofed brand.
Smishing scams, i.e., phishing attacks using SMS, Voice over Internet Protocol (VoIP) network hacking and “vishing”, i.e., voice and phishing scams are also becoming more popular with criminals, particularly because these methods can be difficult for authorities to trace. Hackers break into a VoIP network to eavesdrop, make “free” phone calls, spoof caller IDs, and engage in other exploits. It is extremely difficult for a victim to understand a phone number from a trusted company that was hacked to deliver vishing messages. Encryption is also being used on VoIP to hide mobile malware threats, and methods for dealing with these cyber criminals had to become much more sophisticated.

