MAC Address Flooding – Basic switch security does not stop malicious attacks. Security is a layered process that is essentially never complete. The more aware networking professionals within an organization are regarding security attacks and the dangers they pose, the better. Some types of security attacks are described here, but the details of how some of these attacks work are beyond the scope of this course.
All Catalyst switch models use a MAC address table for Layer 2 switching. The MAC address table in a switch contains the MAC addresses associated with each physical port and the associated VLAN for each port. As a frame arrives on a switch port, the source MAC address is recorded in the MAC address table. The switch then examines the received destination MAC address and looks in the MAC address table to see if it contains the destination MAC address. If an entry already exists for the destination MAC address, the switch forwards the frame to the correct port. If the destination MAC address does not exist in the MAC address table, the switch floods the frame out of every port on the switch, except the port where the frame was received.
The MAC address flooding behavior of a switch for unknown addresses can be used to attack a switch. This type of attack is called a MAC address table overflow attack. MAC address table overflow attacks are sometimes referred to as MAC flooding attacks and CAM table overflow attacks. The following figures show how this type of attack works.
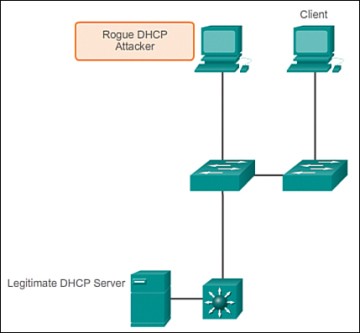
DHCP Spoofing – DHCP is the protocol that automatically assigns a host a valid IP address out of a DHCP pool. DHCP has always been the main protocol used within industry for allocating clients IP addresses. Two types of DHCP attacks can be performed against a switched network: DHCP starvation attacks and DHCP spoofing, as shown in Figure 6.
In DHCP starvation attacks, an attacker floods the DHCP server with DHCP requests to use all the available IP addresses that the DHCP server can issue. After these IP addresses are issued, the server cannot issue any more addresses, and this situation produces a denial-of-service (DoS) attack as new clients cannot obtain network access. A DoS attack is any attack that is used to overload specific devices and network services with illegitimate traffic, thereby preventing legitimate traffic from reaching those resources.
In DHCP spoofing attacks, an attacker configures a fake DHCP server on the network to issue DHCP addresses to clients. The normal reason for this attack is to force the clients to use false Domain Name System (DNS) or Windows Internet Naming Service (WINS) servers and to make the clients use the attacker, or a machine under the control of the attacker, as their default gateway.
DHCP starvation is often used before a DHCP spoofing attack to deny service to the legitimate DHCP server, making it easier to introduce a fake DHCP server into the network.
Leveraging CDP – The Cisco Discovery Protocol (CDP) is a proprietary protocol that all Cisco devices can be configured to use. CDP discovers other Cisco devices that are directly connected, which allows the devices to auto-configure their connection. In some cases, this simplifies configuration and connectivity.
By default, most Cisco routers and switches have CDP enabled on all ports. CDP information is sent in periodic, unencrypted broadcasts. This information is updated locally in the CDP database of each device. Even though CDP is a Layer 2 protocol, all Cisco devices can use CDP to communicate and share device information with an adjacent Cisco device; however, this information cannot be shared beyond a single, adjacent Cisco device.
CDP contains information about the device, such as the IP address, software version, platform, capabilities, and the native VLAN. This information can be used by an attacker to find ways to attack the network, typically in the form of a DoS attack.
Brute Force Password Attack – A brute force password attack tries to crack a password on another device. The first phase of a brute force password attack starts with the attacker using a list of common passwords and a program designed to try to establish a Telnet session using each word on the dictionary list. If the password is not discovered by the first phase, a second phase begins. In the second phase of a brute force attack, the attacker uses a program that creates sequential character combinations in an attempt to guess the password. Given enough time, a brute force password attack can crack almost all passwords used.
Telnet DoS Attack – Telnet can also be used to launch a DoS attack. In a Telnet DoS attack, the attacker exploits a flaw in the Telnet server software running on the switch that renders the Telnet service unavailable. This sort of attack prevents an administrator from remotely accessing switch management functions. This can be combined with other direct attacks on the network as part of a coordinated attempt to prevent the network administrator from accessing core devices during the breach.
Vulnerabilities in the Telnet service that permit DoS attacks to occur are usually addressed in security patches that are included in newer Cisco IOS revisions.
Internet Control Message Protocol Floods
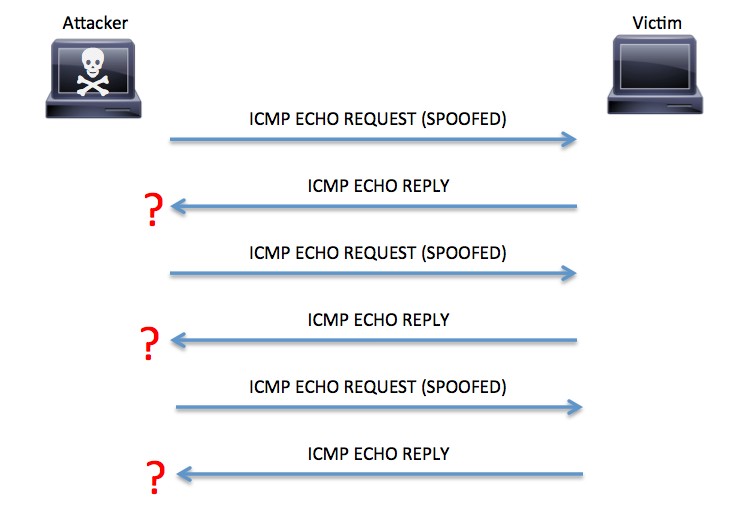
Internet Control Message Protocol (ICMP) flood attacks have existed for many years. They are among the oldest types of DoS attacks. In ICMP flood attacks, the attacker overwhelms the targeted resource with ICMP echo request (ping) packets, large ICMP packets, and other ICMP types to significantly saturate and slow down the victim’s network infrastructure. This is illustrated in figure below.
Smurf Attacks
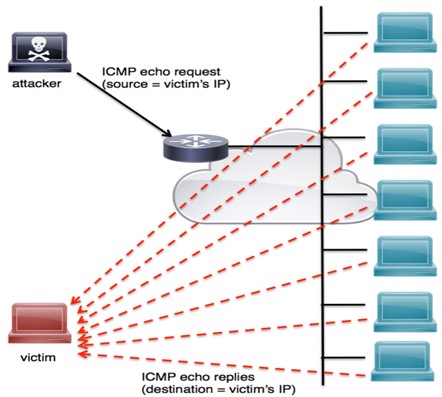
Another type of ICMP-based attack is a smurf attack. The name smurf comes from the original exploit tool source code, smurf.c, created by an individual called TFreak in 1997. In a smurf attack, an attacker broadcasts a large number of ICMP packets with the victim’s spoofed source IP to a network using an IP broadcast address. This causes devices in the network to respond by sending a reply to the source IP address. This exchange is illustrated in Figure 5.
This attack can easily be mitigated on a Cisco IOS device by using the no ip directed-broadcast subinterface command, as shown in the following example:
Router(config)# interface GigabitEthernet 0
Router(config-if)# no ip directed-broadcast
SYN Flood Attacks
When a host (client) initiates a TCP connection to a server, the client and server exchange a series of messages to establish the connection. This connection establishment is called the TCP three-way handshake. This is illustrated in Figure below.
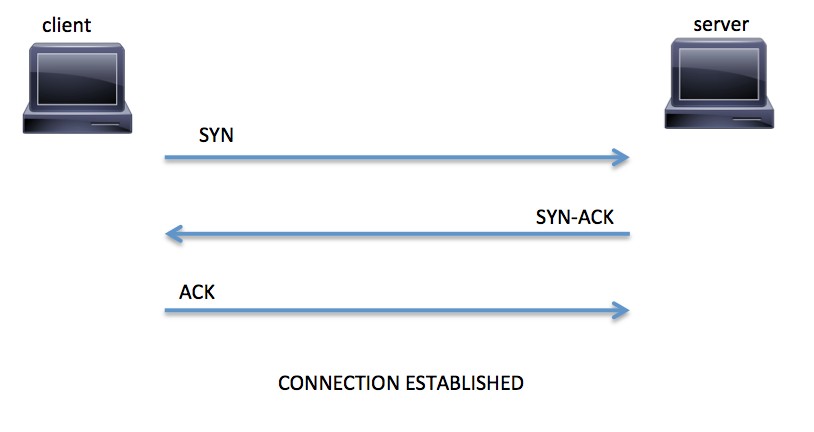
- The client requests a connection by sending a SYN (synchronize) message to the server
- The server acknowledges this request by sending SYN-ACK back to the client
- The client responds with an ACK (acknowledgement) and the connection is established
In a SYN flood attack, the attacker does not reply to the server with the expected ACK. To do this, the attacker can spoof the source IP address or simply not reply to the SYN-ACK. This is illustrated in Figure below.
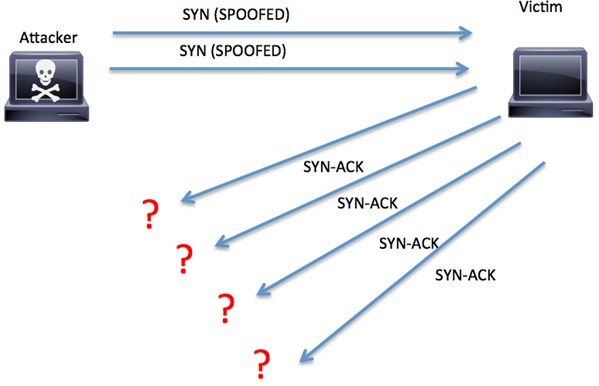
RFC 4987 provides more information about how TCP SYN flood attacks work and common mitigations.
UDP Flood Attacks
Similar to TCP flood attacks, the main goal of the attacker when performing a UDP flood attack is to cause system resource starvation. A UDP flood attack is triggered by sending a large number of UDP packets to random ports on the victim’s system. The system will notice that no application listens at that port and reply with an ICMP destination unreachable packet. Subsequently, if a large number of UDP packets are sent, the victim will be forced to send numerous ICMP packets. In most cases, these attacks are accomplished by spoofing the attacker’s source IP address. Most modern operating systems now limit the rate at which ICMP responses are sent, minimizing the impact and mitigating this type of DDoS attack.
Teardrop Attacks
Teardrop attacks involve sending crafted packets with overlapping, over-sized payloads to the victim system. Modern operating systems are now immune to this attack, but because of a deficiency in the TCP fragmentation and reassembly implementation of older operating systems, this attack caused a crash of those systems.

