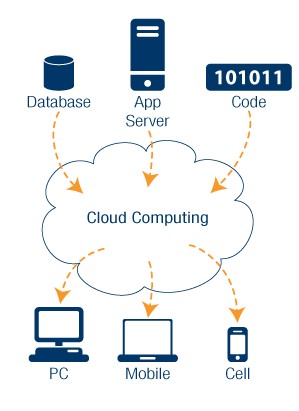
Cloud Computing is a modern technology which is based on internet. It uses the internet and central remote servers to maintain data and application, or you can say, it uses the computer resources that are delivered as a service over the internet. The Cloud Computing can be called as the next stage in the evolution of internet.
Cloud Types
Cloud computing can be divided into three different models: public, hybrid, and private. While the three models have common traits, they also have different key features that make one model a better choice to meet business’ IT needs.
- The Private Cloud – The Private Cloud is dedicated to private infrastructure. You can consider your personal data centre setup as a Private Cloud IaaS. But unless the cloud infrastructure (virtualization, storage, extreme redundancy, etc.) is present, it is not considered as a cloud, but the basic concept is same. Two examples of private cloud solutions are VMware vCloud and Citrix VDI. It is also called “internal cloud computing,” and is the next generation of virtualization.
- The Public Cloud – The Public Cloud is dedicated completely to hosted solution. Here no hardware is owed by the user. It is the traditional model that everyone thinks of when they envision cloud computing. Vendors dynamically allocate computing resources (hard drive space, RAM, and processor power) on a per-user basis through web applications. Salesforce.com and ADP are two well-known vendors that offer public cloud computing services.
- The Hybrid Cloud – The Hybrid Cloud combines the concept of both Private as well as Public. Most company evolved into this type of cloud from a traditional, private hardware infrastructure to a cloud-based one. Generally, business applications like Exchange Server 2007 or Microsoft Dynamics will interact with a vendor-hosted service. For example, Cisco, offers IronPort Email Security as their hybrid solution and Google, known for hosted solution, offers Postini email archiving.
Mixing of Private Cloud with Public Cloud is the best solution for you and your customer. It intermingle the privacy of a traditional data centre with the hosted cloud infrastructure. It can be said that, companies will transition their data recovery efforts to the Public Cloud while retaining production and operations in-house by a Private Cloud.
Experts and analysts predicted that by the end of 2012, around 20% of businesses will exist completely in the Public Cloud.
Cloud Service Models
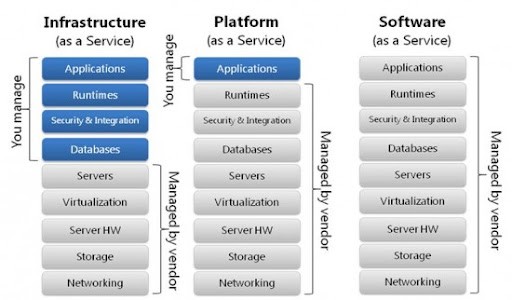
Figure 2: Models of cloud
The basic cloud service models are as follows
Infrastructure as a Service (IaaS) – Infrastructure as a Service (IaaS) is that part of cloud computing that allows leasing and managing computing infrastructure for business needs. This consists of virtual machines (VMs) run as guests by a hypervisor, like Xen or KVM with operating system, middleware, network, storage, data and applications.
The vendor also supplies a management interface in which one can interact with the Services. Payment for computing resources in done with respect to number of User’s system, time duration (generally per hour), usage of bandwidth (generally in gigabyte), storage(generally in gigabyte) or combination of any.
IaaS cloud providers and vendors provide the physical hardware that they own and manage in the backhand, supply on demand from large pools in data centers. Examples of IaaS include: Amazon CloudFormation (and underlying services such as Amazon EC2), Rackspace Cloud, Terremark and Google Compute Engine. User installs operating system images on the machines as well as needed application software. The end user is responsible for patching and maintaining the operating systems and application software.
Platform as a Service (PaaS) – Platform as a Service are development platforms for which the development tool itself is hosted in the cloud and accessed through a browser. With PaaS, developer can build web applications without installing any tools on their computer and then deploy those applications without any specialized systems administration skills. PaaS service providers deliver a computing platform with operating system, programming execution environment, database, and web server. The computer and storage resources scale automatically to match application demand in PaaS.
The alternative to PaaS is to develop web applications using desktop development tools like Eclipse, and then manually deploy those applications to a cloud hosting provider. PaaS requires the following elements as a minimum requirement
- Browser-based development studio – If you have to install something on your computer to develop applications.
- Seamless deployment to hosted runtime environment – Ideally, a developer should be able to deploy a PaaS application with one click.
- Management and monitoring tools – While cloud-based solutions are very cost effective, but are tricky to manage and scale without good tools. Hence, monitoring tools to monitor cloud application are needed.
- Pay as you go billing – Avoiding upfront costs has made PaaS popular as payment is based on actual usage of resources.
PaaS platforms also have functional differences from traditional development platforms. These include.
- Multi-tenant development tool: traditional development tools are single user – a cloud-based studio must support multiple users, each with multiple active projects.
- Multi-tenant deployment architecture: scalability is often not a concern of the initial development effort and is left instead for the administrators to deal with when the project deploys. In PaaS, scalability of the application and data tiers must be built-in (e.g., load balancing, failover need to be basic elements of the dev platform itself).
- Integrated management: traditional development solution usually does not concern themselves with runtime monitoring, but in PaaS, the monitoring ability needs to be integrated into the development platform.
- Integrated billing: PaaS offerings require mechanisms for billing based on usage that are unique to the SaaS world.
The benefits of PaaS depend upon the people who can develop, maintain and deploy web applications. Building web applications requires expert developer with three, highly specialized skill sets
- Back end server development (e.g., Java/J2EE)
- Front end client development (e.g., Javascript/Dojo)
- Web site administration.
Examples of PaaS include
- App Engine from Google: based on Python and Django
- com from SalesForce: based on the SalesForce SaaS infrastructure and Apex language
- Bungee Connect: visual development studio based on Java
- Long Jump: based on Java/Eclipse
- Wave Maker: visual development studio based on Java and hosted on Amazon EC2
Software as a Service – Software as a Service (SaaS), works as a software supplier. It is a software supplying model where software and data are hosted on the cloud. SaaS is accessed by users via web browser.
SaaS in the present technical industry have become a common delivery model for many business applications, including accounting, collaboration, customer relationship management (CRM), management information systems (MIS), enterprise resource planning (ERP), invoicing, human resource management (HRM), content management (CM) and service desk management. One of the biggest selling points for these companies is the potential to reduce IT support costs by outsourcing hardware and software maintenance and support to the SaaS provider.
Centralized hosting of business applications dates back to the 1960s. Starting in that decade, IBM and other mainframe providers conducted a service bureau business often referred to as time sharing or utility computing. Such services included offering computing power and database storage to banks and other large organizations from their worldwide data centers.
Software as a service essentially extends the idea of the ASP (Application Service Provider) model. The term Software as a Service (SaaS), however, is commonly used in more specific settings.
Unlike the traditional software which is sold as a perpetual license with an upfront cost in the market, SaaS provides price applications using a subscription fee, mostly a monthly or yearly fee. The initial setup cost for SaaS is typically lower than the equivalent commonly used software. SaaS vendors typically price their applications on the basis of usage parameters.
In SaaS model, a free service is made available with limited functionality, and fees are charged for enhanced functionality. Some other SaaS applications are completely free to users, with revenue being derived from alternate sources such as advertising.
With SaaS model, a single version of the application, with a single configuration, is used for all customers. In some cases, a second version of the application is set up to enable a select group of customers with access to pre-release versions of the applications for testing purposes. This is advantage with traditional software, where multiple physical copies of the software, each potentially of a different version, with a potentially different configuration, and oftentimes customized, are installed across various customer sites.
SaaS applications support application customization, i.e., users can set their own configuration that satisfies their functionality and appearance. Each user can have their own settings for the configuration options.
Cloud Security
Cloud computing security or cloud security is a part of information security. It refers to policies, technologies and controls deployed to protect data, applications, and the resources of cloud computing being used by organization.
There are a number of security issues with cloud computing faced either by cloud providers or their customers. The cloud service provider must ensure that their infrastructure is secure and clients’ data and applications are protected while the customer must ensure that the provider has taken the proper security measures to protect their information.
Threats And Security Issues
- Abuse and Nefarious Use of Cloud Computing
- Insecure Application Programming Interfaces
- Malicious Insiders
- Shared Technology Vulnerabilities
- Data Loss/Leakage
- Account, Service & Traffic Hijacking
- Unknown Risk Profile

