Various types of attacks on routers are usually sophisticated types of DDoS attacks and which includes
Proxy
Because ACLs cannot distinguish between legitimate and malicious SYNs coming from the same source IP or proxy, it would, by definition, have to block all the victim’s clients coming from a certain source IP or proxy when attempting to stop this focused spoofed attack.
Application-level (client) attacks
Although ACLs could theoretically block client attacks such as HTTP error and HTTP half-open connection attacks (provided the attack and individual non-spoofed sources could be accurately detected), it would require users to configure hundreds and sometimes thousands of ACLs per victim.
Internet Control Message Protocol Floods
Internet Control Message Protocol (ICMP) flood attacks have existed for many years. They are among the oldest types of DoS attacks. In ICMP flood attacks, the attacker overwhelms the targeted resource with ICMP echo request (ping) packets, large ICMP packets, and other ICMP types to significantly saturate and slow down the victim’s network infrastructure. This is illustrated in figure below.
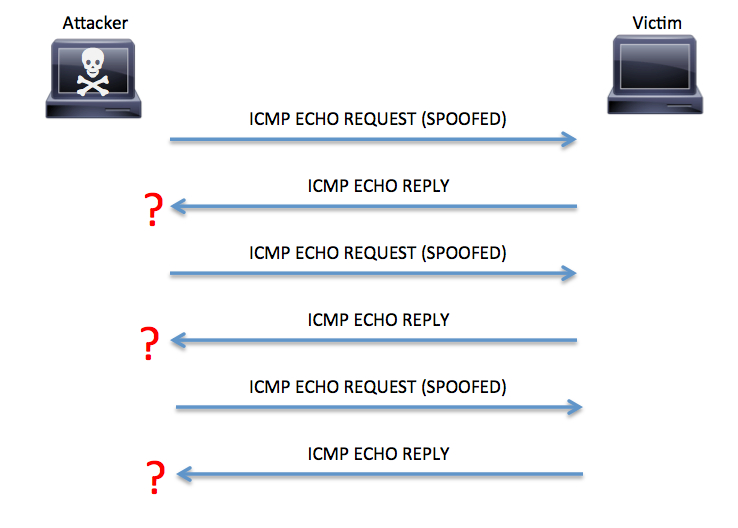
Figure ICMP Flood Example
Smurf Attacks
Another type of ICMP-based attack is a smurf attack. The name smurf comes from the original exploit tool source code, smurf.c, created by an individual called TFreak in 1997. In a smurf attack, an attacker broadcasts a large number of ICMP packets with the victim’s spoofed source IP to a network using an IP broadcast address. This causes devices in the network to respond by sending a reply to the source IP address. This exchange is illustrated in Figure 5.
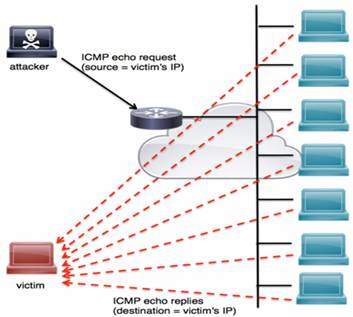
Figure 5. Smurf Attack
This attack can easily be mitigated on a Cisco IOS device by using the no ip directed-broadcast subinterface command, as shown in the following example:
Router(config)# interface GigabitEthernet 0
Router(config-if)# no ip directed-broadcast
SYN Flood Attacks
When a host (client) initiates a TCP connection to a server, the client and server exchange a series of messages to establish the connection. This connection establishment is called the TCP three-way handshake. This is illustrated in Figure below.
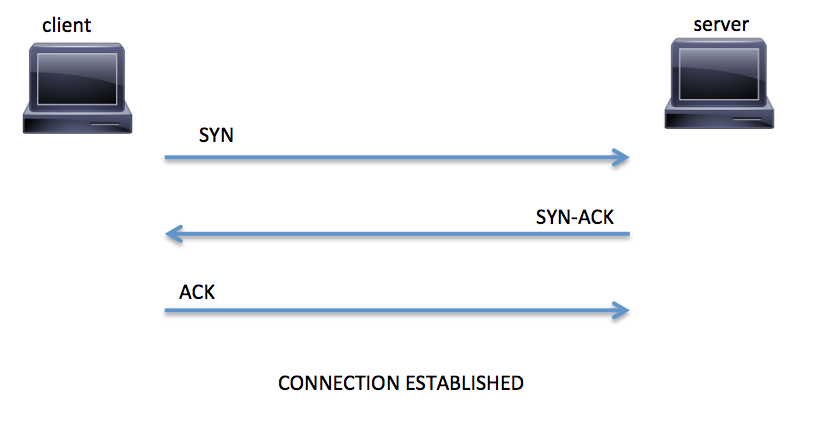
Figure TCP Three-Way Handshake
- The client requests a connection by sending a SYN (synchronize) message to the server
- The server acknowledges this request by sending SYN-ACK back to the client
- The client responds with an ACK (acknowledgement) and the connection is established
In a SYN flood attack, the attacker does not reply to the server with the expected ACK. To do this, the attacker can spoof the source IP address or simply not reply to the SYN-ACK. This is illustrated in Figure below.
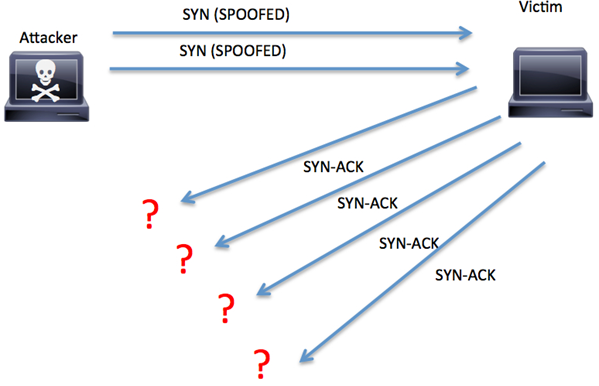
Figure SYN Flood Example
RFC 4987 provides more information about how TCP SYN flood attacks work and common mitigations.
UDP Flood Attacks
Similar to TCP flood attacks, the main goal of the attacker when performing a UDP flood attack is to cause system resource starvation. A UDP flood attack is triggered by sending a large number of UDP packets to random ports on the victim’s system. The system will notice that no application listens at that port and reply with an ICMP destination unreachable packet. Subsequently, if a large number of UDP packets are sent, the victim will be forced to send numerous ICMP packets. In most cases, these attacks are accomplished by spoofing the attacker’s source IP address. Most modern operating systems now limit the rate at which ICMP responses are sent, minimizing the impact and mitigating this type of DDoS attack.
Teardrop Attacks
Teardrop attacks involve sending crafted packets with overlapping, over-sized payloads to the victim system. Modern operating systems are now immune to this attack, but because of a deficiency in the TCP fragmentation and reassembly implementation of older operating systems, this attack caused a crash of those systems.
DNS Amplification Attacks
A Domain Name System (DNS) request can be recursive or nonrecursive (or iterative). Client applications, such as Internet browsers, typically request that the DNS server perform recursion by setting a Recursion Desired (RD) flag in the DNS request packet. If the DNS server cannot answer the request either from its cache or zone information, the server will request assistance from other DNS servers.
Unfortunately, many recursive name servers accept DNS queries from any source. In addition, many DNS implementations allow recursion by default, even when the name server is anticipated to serve only authoritative requests. This is known as an open resolver. DNS open resolvers are vulnerable to multiple malicious attacks, such as DNS cache poisoning and DDoS attacks.
A DNS amplification attack is the most common DDoS attack that uses recursive name servers, although some DNS amplifications attacks may not require a recursive server to be successful. DNS amplification attacks are similar to smurf attacks. In a smurf attack, an attacker can send spoofed ICMP echo requests (type 8) to create a DoS condition. In a DNS amplification DDoS attacker, an attacker sends small, spoofed address queries to an open resolver, causing it to send much larger responses to the spoofed-address target. Subsequently, the resolver contributes to the DDoS attack on spoofed addresses. Figure below illustrates the basic steps of a DNS amplification DDoS attack.
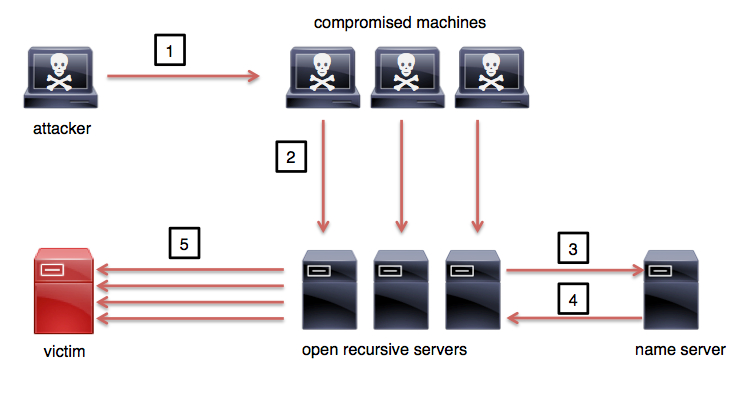
Figure DNS Amplification Attack
The following steps are illustrated in Figure
- The attacker triggers and directs the compromised machines to begin the attack
- The compromised machines send a DNS query for the domain com and set the source IP address to the victim’s IP address
- The open resolver servers ask the upstream name server(s) the location of com
- The name server sends a reply back to the open recursive servers
- The open recursive servers send DNS responses to the victim
SIP INVITE Flood Attacks
The Session Initiation Protocol (SIP) is a VoIP standard defined in RFC 3261. SIP INVITE messages are used to establish a media session between user and calling agents. In SIP INVITE flood attacks, the attacker sends numerous (often spoofed) INVITE messages to the victim, causing network degradation or a complete DoS condition.
Encrypted SSL DDoS Attacks
Encrypted (SSL-based) DDoS attacks are becoming more prevalent because they allow attackers to gain the following advantages
- Encrypted DDoS attacks consume more CPU resources during the encryption and decryption process. Consequently, they amplify the impact on the victim system or network.
- Numerous DDoS mitigation technologies do not support decryption of SSL traffic. A large number of these attacks cannot be scrubbed.
Slowloris
Slowloris is an attack tool created by RSnake (Robert Hansen) that tries to keep numerous connections open on a web server. The attack works by opening connections on the victim’s server and sending a partial request. Intermittently, the attack sends subsequent HTTP headers. However, the attack does not complete the request to maintain these connections as open until the victim is not able to process requests from legitimate clients. Similar attack tools and methodologies exist. The following are a few examples
- PyLoris
- QSlowloris (a variant of Slowloris for Windows)
- slowhttptest
Low Orbit Ion Cannon and High Orbit Ion Canon
Low Orbit Ion Cannon (LOIC) and High Orbit Ion Canon (HOIC) have become popular DDoS tools for hacktivist groups such as Anonymous and the Syrian Electronic Army. These tools allow even nontechnical people to create a DDoS attack with a few clicks using their own computers instead of the traditional bot-served attacks.
Best practices and counter measures
Every router must meet the following configuration for as best practices
- No local user accounts are configured on the router. Routers and switches must use TACACS+ for all user authentication.
- The enable password on the router or switch must be kept in a secure encrypted form. The router or switch must have the enable password set to the current production router/switch password from the device’s support organization.
- The following services or features must be disabled
- IP directed broadcasts
- Incoming packets at the router/switch sourced with invalid addresses such as RFC1918 addresses
- TCP small services
- UDP small services
- All source routing and switching
- All web services running on router
- Cisco discovery protocol on Internet connected interfaces
- Telnet, FTP, and HTTP services
- Auto-configuration
- The following services should be disabled unless a business justification is provided
- Cisco discovery protocol and other discovery protocols
- Dynamic trunking
- Scripting environments, such as the TCL shell
- The following services must be configured
- Password-encryption
- NTP configured to a corporate standard source
- All routing updates shall be done using secure routing updates.
- Use corporate standardized SNMP community strings. Default strings, such as public or private must be removed. SNMP must be configured to use the most secure version of the protocol allowed for by the combination of the device and management systems.
- Access control lists must be used to limit the source and type of traffic that can terminate on the device itself.
- Access control lists for transiting the device are to be added as business needs aris
- The router must be included in the corporate enterprise management system with a designated point of contact.
- Each router must have the following statement presented for all forms of login whether remote or local:
“UNAUTHORIZED ACCESS TO THIS NETWORK DEVICE IS PROHIBITED. You must
have explicit permission to access or configure this device. All activities performed on
this device may be logged, and violations of this policy may result in disciplinary action,
and may be reported to law enforcement. There is no right to privacy on this device. Use
of this system shall constitute consent to monitoring.”
- Telnet may never be used across any network to manage a router, unless there is a secure tunnel protecting the entire communication path. SSH version 2 is the preferred management protocol.
- Dynamic routing protocols must use authentication in routing updates sent to neighbors. Password hashing for the authentication string must be enabled when supported.
- The corporate router configuration standard will define the category of sensitive routing and switching devices, and require additional services or configuration on sensitive devices including
- IP access list accounting
- Device logging
- Incoming packets at the router sourced with invalid addresses, such as RFC1918 addresses, or those that could be used to spoof network traffic shall be dropped
- Router console and modem access must be restricted by additional security controls

