Risk is potential of losing something of value. Values (such as physical health, social status, emotional well being or financial wealth) can be gained or lost when taking risk resulting from a given action, activity and/or inaction, foreseen or unforeseen. Risk can also be defined as the intentional interaction with uncertainty. Uncertainty is a potential, unpredictable, unmeasurable and uncontrollable outcome, risk is a consequence of action taken in spite of uncertainty.
Risks exist because entities, companies and organisations have “assets” of a material or immaterial nature that could be subject to damage that has consequences on the entity in question.
Assets
In very general terms, an asset can be defined as anything that could be of value or
importance to the entity. In information security, the ISO/IEC 27005 standard distinguishes between:
- Primary assets including – Processes and activities, Information
- Supporting assets including – Equipment, Software, Networks, Personnel, Premises, Organisational support
Risks (and their consequences) differ depending on what type of damage occurs. Different categories of assets will be damaged in different ways, and while it is easy to list the ways in which information can be damaged (by being lost, tampered with or exposed, among other things), few standard classifications exist for processes or certain support-related assets.
The type of damage an asset sustains is not clearly specified in the ISO/IEC 27005 standard, which does not distinguish either damage from consequences. In our view however it is important to distinguish between direct consequences of damage to assets, and secondary or indirect consequences affecting processes and the entity’s activities.
Risk management is the identification, assessment, and prioritization of risks (defined in ISO 31000 as the effect of uncertainty on objectives) followed by coordinated and economical application of resources to minimize, monitor, and control the probability and/or impact of unfortunate events or to maximize the realization of opportunities. Risk management’s objective is to assure uncertainty does not deflect the endeavor from the business goals.
For the most part, these methods consist of the following elements, performed, more or less, in the following order.
- identify, characterize threats
- assess the vulnerability of critical assets to specific threats
- determine the risk (i.e. the expected likelihood and consequences of specific types of attacks on specific assets)
- identify ways to reduce those risks
- prioritize risk reduction measures based on a strategy
Process
According to the standard ISO 31000 “Risk management – Principles and guidelines on implementation,” the process of risk management consists of several steps as follows:
Establishing the context – This involves:
- identification of risk in a selected domain of interest
- planning the remainder of the process
- mapping out the following:
- the social scope of risk management
- the identity and objectives of stakeholders
- the basis upon which risks will be evaluated, constraints.
- defining a framework for the activity and an agenda for identification
- developing an analysis of risks involved in the process
- mitigation or solution of risks using available technological, human and organizational resources.
Identification – After establishing the context, the next step in the process of managing risk is to identify potential risks. Risks are about events that, when triggered, cause problems or benefits. Hence, risk identification can start with the source of our problems and those of our competitors (benefit), or with the problem itself.
- Source analysis – Risk sources may be internal or external to the system that is the target of risk management (use mitigation instead of management since by its own definition risk deals with factors of decision-making that cannot be managed). Examples of risk sources are: stakeholders of a project, employees of a company or the weather over an airport.
- Problem analysis – Risks are related to identified threats. For example: the threat of losing money, the threat of abuse of confidential information or the threat of human errors, accidents and casualties. The threats may exist with various entities, most important with shareholders, customers and legislative bodies such as the government.
When either source or problem is known, the events that a source may trigger or the events that can lead to a problem can be investigated. For example: stakeholders withdrawing during a project may endanger funding of the project; confidential information may be stolen by employees even within a closed network; lightning striking an aircraft during takeoff may make all people on board immediate casualties.
The chosen method of identifying risks may depend on culture, industry practice and compliance. The identification methods are formed by templates or the development of templates for identifying source, problem or event. Common risk identification methods are:
- Objectives-based risk identification – Organizations and project teams have objectives. Any event that may endanger achieving an objective partly or completely is identified as risk.
- Scenario-based risk identification – In scenario analysis different scenarios are created. The scenarios may be the alternative ways to achieve an objective, or an analysis of the interaction of forces in, for example, a market or battle. Any event that triggers an undesired scenario alternative is identified as risk – see Futures Studies for methodology used by Futurists.
- Taxonomy-based risk identification – The taxonomy in taxonomy-based risk identification is a breakdown of possible risk sources. Based on the taxonomy and knowledge of best practices, a questionnaire is compiled. The answers to the questions reveal risks.
- Common-risk checking – In several industries, lists with known risks are available. Each risk in the list can be checked for application to a particular situation.
- Risk charting – This method combines the above approaches by listing resources at risk, threats to those resources, modifying factors which may increase or decrease the risk and consequences it is wished to avoid. Creating a matrix under these headings enables a variety of approaches. One can begin with resources and consider the threats they are exposed to and the consequences of each. Alternatively one can start with the threats and examine which resources they would affect, or one can begin with the consequences and determine which combination of threats and resources would be involved to bring them about.
Threat-based definitions of risk usually involve selecting, from a list of typical threats, standard elements that are relevant to the type of asset in question. For the asset elements of the three examples listed above, there would be (based on just some examples from ISO/IEC 27005)
- Strategic document – Related threats are Media or document theft , Disclosure
- Database – Related threats are Tampering using software , Software malfunction
- Data server – Related threats are Fire , Water damage , Serious accident , Destruction of equipment , Flooding
Assessment
Once risks have been identified, they must then be assessed as to their potential severity of impact (generally a negative impact, such as damage or loss) and to the probability of occurrence. These quantities can be either simple to measure, in the case of the value of a lost building, or impossible to know for sure in the case of the probability of an unlikely event occurring. Therefore, in the assessment process it is critical to make the best educated decisions in order to properly prioritize the implementation of the risk management plan.
Even a short-term positive improvement can have long-term negative impacts. Take the “turnpike” example. A highway is widened to allow more traffic. More traffic capacity leads to greater development in the areas surrounding the improved traffic capacity. Over time, traffic thereby increases to fill available capacity. Turnpikes thereby need to be expanded in a seemingly endless cycles. There are many other engineering examples where expanded capacity (to do any function) is soon filled by increased demand. Since expansion comes at a cost, the resulting growth could become unsustainable without forecasting and management.
The fundamental difficulty in risk assessment is determining the rate of occurrence since statistical information is not available on all kinds of past incidents. Furthermore, evaluating the severity of the consequences (impact) is often quite difficult for intangible assets. Asset valuation is another question that needs to be addressed. Thus, best educated opinions and available statistics are the primary sources of information. Nevertheless, risk assessment should produce such information for the management of the organization that the primary risks are easy to understand and that the risk management decisions may be prioritized. Thus, there have been several theories and attempts to quantify risks. Numerous different risk formulae exist, but perhaps the most widely accepted formula for risk quantification is:
Rate (or probability) of occurrence multiplied by the impact of the event equals risk magnitude.
Since risk assessment and management is essential in security management, both are tightly related. Security assessment methodologies like CRAMM contain risk assessment modules as an important part of the first steps of the methodology. On the other hand, risk assessment methodologies like Mehari evolved to become security assessment methodologies. An ISO standard on risk management (Principles and guidelines on implementation) was published under code ISO 31000 on 13 November 2009.
Quantitative Analysis – There are many formal methods used to “measure” risk.
Often the probability of a negative event is estimated by using the frequency of past similar events. Probabilities for rare failures may be difficult to estimate. This makes risk assessment difficult in hazardous industries, for example nuclear energy, where the frequency of failures is rare, while harmful consequences of failure are severe.
Statistical methods may also require the use of a cost function, which in turn may require the calculation of the cost of loss of a human life. This is a difficult problem. One approach is to ask what people are willing to pay to insure against death or radiological release (e.g. GBq of radio-iodine), but as the answers depend very strongly on the circumstances it is not clear that this approach is effective.
Risk is often measured as the expected value of an undesirable outcome. This combines the probabilities of various possible events and some assessment of the corresponding harm into a single value. See also Expected utility. The simplest case is a binary possibility of Accident or No accident. The associated formula for calculating risk is then:
![]()
For example, if performing activity X has a probability of 0.01 of suffering an accident of A, with a loss of 1000, then total risk is a loss of 10, the product of 0.01 and 1000.
Situations are sometimes more complex than the simple binary possibility case. In a situation with several possible accidents, total risk is the sum of the risks for each different accident, provided that the outcomes are comparable:
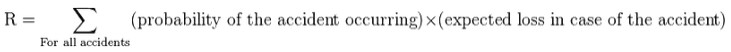
For example, if performing activity X has a probability of 0.01 of suffering an accident of A, with a loss of 1000, and a probability of 0.000001 of suffering an accident of type B, with a loss of 2,000,000, then total loss expectancy is 12, which is equal to a loss of 10 from an accident of type A and 2 from an accident of type B.
The risk estimation step leads to an evaluation of the impact (I) and the probability (P) of each risk. The only task remaining is to give an overall mark or, simply, to establish a range of risk acceptability. The easily accessible nature of the two basic concepts makes it easy for management to deal with this aspect. A possible decision-making tool could be – A function of Seriousness of a risk S = f(P,I) and an acceptability table as a function of P and I, like the one below for example.
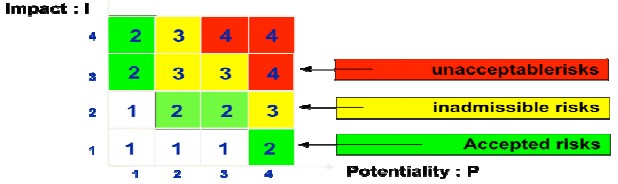
Risk Treatments
Once risks have been identified and assessed, all techniques to manage the risk fall into one or more of these four major categories:
- Avoidance (eliminate, withdraw from or not become involved) – As the circumstances in which each risk may occur are completely defined, it is possible for the activity, project or process managers to directly manage the solutions to be implemented and this often proves to be economical. Considering the scenario of a confidential strategic document being diverted while it is printed on a shared printer. The decision could be to simply modify the process and print this same document locally on a printer that isn’t shared, rather than having to secure the printing process on a shared printer.
- Reduction (optimize – mitigate) – Here it is important to know what level of detail is considered with such a risk management method. This is because decisions on how to treat risks, and possible orientations can be linked to different levels of detail.
- Sharing (transfer – outsource or insure) – It refers to an agreement between the entity and one or more third parties to share certain responsibilities. The most typical example is that of insurance, but many other kinds of agreements are possible.
- Retention (accept and budget)
Risk Management Plan
Risk mitigation needs to be approved by the appropriate level of management. For instance, a risk concerning the image of the organization should have top management decision behind it whereas IT management would have the authority to decide on computer virus risks.
The risk management plan should propose applicable and effective security controls for managing the risks. For example, an observed high risk of computer viruses could be mitigated by acquiring and implementing antivirus software. A good risk management plan should contain a schedule for control implementation and responsible persons for those actions.
According to ISO/IEC 27001, the stage immediately after completion of the risk assessment phase consists of preparing a Risk Treatment Plan, which should document the decisions about how each of the identified risks should be handled. Mitigation of risks often means selection of security controls, which should be documented in a Statement of Applicability, which identifies which particular control objectives and controls from the standard have been selected, and why.

