UNIX is an operating system which was first developed in the 1960s, and has been under constant development ever since. By operating system, we mean the suite of programs which make the computer work. It is a stable, multi-user, multi-tasking system for servers, desktops and laptops.
UNIX systems also have a graphical user interface (GUI) similar to Microsoft Windows which provides an easy to use environment. However, knowledge of UNIX is required for operations which aren’t covered by a graphical program, or for when there is no windows interface available, for example, in a telnet session.
There are many different versions of UNIX, although they share common similarities. The most popular varieties of UNIX are Sun Solaris, GNU/Linux, and MacOS X. Linux is a Unix-like and mostly POSIX-compliant computer operating system (OS) assembled under the model of free and open-source software development and distribution. The defining component of Linux is the Linux kernel, an operating system kernel first released on 5 October 1991 by Linus Torvalds. The Free Software Foundation uses the name GNU/Linux to describe the operating system, which has led to some controversy.
Linux was originally developed as a free operating system for personal computers based on the Intel x86 architecture, but has since been ported to more computer hardware platforms than any other operating system. Thanks to its dominance on smartphones, Android, which is built on top of the Linux kernel, has the largest installed base of all general-purpose operating systems. Linux, in its original form, is also the leading operating system on servers and other big iron systems such as mainframe computers and supercomputers
The LINUX operating system is made up of – the kernel and the shell.
The Kernel – The kernel of UNIX is the hub of the operating system: it allocates time and memory to programs and handles the filestore and communications in response to system calls.
As an illustration of the way that the shell and the kernel work together, suppose a user types rm myfile (which has the effect of removing the file myfile). The shell searches the filestore for the file containing the program rm, and then requests the kernel, through system calls, to execute the program rm on myfile. When the process rm myfile has finished running, the shell then returns the UNIX prompt % to the user, indicating that it is waiting for further commands.
The Shell – The shell acts as an interface between the user and the kernel. When a user logs in, the login program checks the username and password, and then starts another program called the shell. The shell is a command line interpreter (CLI). It interprets the commands the user types in and arranges for them to be carried out. The commands are themselves programs: when they terminate, the shell gives the user another prompt (% on our systems).
The adept user can customise his/her own shell, and users can use different shells on the same machine. Staff and students in the school have the tcsh shell by default. The tcsh shell has certain features to help the user inputting commands.
- Filename Completion – By typing part of the name of a command, filename or directory and pressing the [Tab] key, the tcsh shell will complete the rest of the name automatically. If the shell finds more than one name beginning with those letters you have typed, it will beep, prompting you to type a few more letters before pressing the tab key again.
- History – The shell keeps a list of the commands you have typed in. If you need to repeat a command, use the cursor keys to scroll up and down the list or type history for a list of previous commands.
Just like Windows XP, Windows 7, Windows 8, and Mac OS X, Linux is an operating system. An operating system is software that manages all of the hardware resources associated with your desktop or laptop. To put it simply – the operating system manages the communication between your software and your hardware. Without the operating system (often referred to as the “OS”), the software wouldn’t function. The Linux OS is comprised of a number of pieces:
- The Bootloader: The software that manages the boot process of your computer. For most users, this will simply be a splash screen that pops up and eventually goes away to boot into the operating system.
- The kernel: This is the one piece of the whole that is actually called “Linux”. The kernel is the core of the system and manages the CPU, memory, and peripheral devices. The kernel is the “lowest” level of the OS.
- Daemons: These are background services (printing, sound, scheduling, etc) that either start up during boot, or after you log into the desktop.
- The Shell: You’ve probably heard mention of the Linux command line. This is the shell – a command process that allows you to control the computer via commands typed into a text interface. This is what, at one time, scared people away from Linux the most (assuming they had to learn a seemingly archaic command line structure to make Linux work). This is no longer the case. With modern desktop Linux, there is no need to ever touch the command line.
- Graphical Server: This is the sub-system that displays the graphics on your monitor. It is commonly referred to as the X server or just “X”.
- Desktop Environment: This is the piece of the puzzle that the users actually interact with. There are many desktop environments to choose from (Unity, GNOME, Cinnamon, Enlightenment, KDE, XFCE, etc). Each desktop environment includes built-in applications (such as file managers, configuration tools, web browsers, games, etc).
- Applications: Desktop environments do not offer the full array of apps. Just like Windows and Mac, Linux offers thousands upon thousands of high-quality software titles that can be easily found and installed. Most modern Linux distributions (more on this in a moment) include App Store-like tools that centralize and simplify application installation. For example: Ubuntu Linux has the Ubuntu Software Center which allows you to quickly search among the thousands of apps and install them from one centralized location.
Linux is also distributed under an open source license. Open source follows the following key philosophies:
- The freedom to run the program, for any purpose.
- The freedom to study how the program works, and change it to make it do what you wish.
- The freedom to redistribute copies so you can help your neighbor.
- The freedom to distribute copies of your modified versions to others.
Linux has a number of different versions to suit nearly any type of user. From new users to hard-core users, you’ll find a “flavor” of Linux to match your needs. These versions are called distributions (or, in the short form, “distros.”) Nearly every distribution of Linux can be downloaded for free, burned onto disk (or USB thumb drive), and installed (on as many machines as you like). The most popular Linux distributions are Ubuntu Linux, Linux Mint, Arch Linux, Fedora, Debian and openSUSE.
Each distribution has a different take on the desktop. Some opt for very modern user interfaces (such as Ubuntu’s Unity, above, and Deepin’s Deepin Desktop), whereas others stick with a more traditional desktop environment (openSUSE uses KDE).
Files and processes
Everything in LINUX is either a file or a process. A process is an executing program identified by a unique PID (process identifier). A file is a collection of data. They are created by users using text editors, running compilers etc. Examples of files:
- a document (report, essay etc.)
- the text of a program written in some high-level programming language
- instructions comprehensible directly to the machine and incomprehensible to a casual user, for example, a collection of binary digits (an executable or binary file);
- a directory, containing information about its contents, which may be a mixture of other directories (subdirectories) and ordinary files.
The Directory Structure
All the files are grouped together in the directory structure. The file-system is arranged in a hierarchical structure, like an inverted tree. The top of the hierarchy is traditionally called root (written as a slash / )
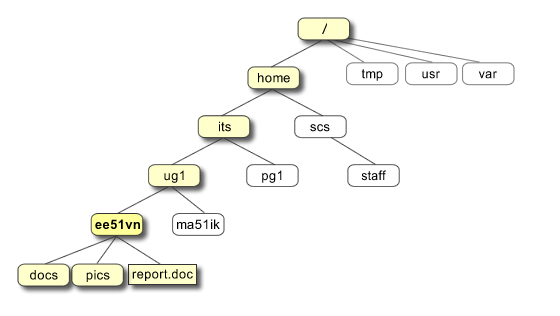
In the diagram above, we see that the home directory of the undergraduate student “ee51vn” contains two sub-directories (docs and pics) and a file called report.doc. The full path to the file report.doc is “/home/its/ug1/ee51vn/report.doc”
Slashes are used to separate directory names in Linux. Physical drives are handled differently than DOS. The /usr directory could be on a separate hard disk, or /mnt might contain a folder named /storage that is actually a drive from another computer. Some of the more common directories found on a Linux system are
- / Represents the root directory.
- /bin Contains common Linux user commands, such as ls, sort, date, and chmod.
- /dev Contains files representing access points to devices on your systems. These can include floppy disks, hard disks, and CD-ROMs.
- /etc Contains administrative configuration files, the passwd file, and the shadow file.
- /home Contains user home directories.
- /mnt Provides a location for mounting devices, such as CD-ROMs and USB drives.
- /sbin Contains administrative commands and daemon processes.
- /usr Contains user documentation, graphical files, libraries, as well as a variety of other user and administrative commands and files.
Directories and files on a Linux system are set up so that access can be controlled. When you log in to the system, you are identified by a user account. In addition to your user account, you might belong to a group or groups. Therefore, files can have permissions set for a user, a group, or others. For example, Red Hat Linux supports three default groups: super users, system users, and normal users. Access for each of these groups has three options – Read, Write and Execute.
To see the current permissions, owner, and group for a file or directory, type the ls -l command. This will display the contents of the directory you are in with the privileges for the user, group, and all others. For example, the list of a file called demofile and the directory demodir would resemble the following
drwxr-xr-x 2 abc users 32768 Nov 20 00:31 demodir
-rw-r–r– 1 abc users 4108 Nov 16 11:21 demofile
The permissions are listed in the first column. The first letter is whether the item is a directory or a file. If the first letter is d, the item is a directory, as in the first item listed previously, demodir. For the file demofile, the first letter is -. The next nine characters denote access and take the following form, rwx|rwx|rwx. The first three list the access rights of the user, so for demodir, the user has read, write, and execute privileges. The next three bits denote the group rights; therefore, the group has read and execute privileges for the demodir folder. Finally, the last three bits specify the access all others have to the demodir folder. In this case, they have read and execute privileges. The third column, abc, specifies the owner of the file/directory, and the fourth column, users, is the name of the group for the file/directory. The only one who can modify or delete any file in this directory is the owner abc.
The chmod command is used by a file owner or administrator to change the definition of access permissions to a file or set of files. Chmod can be used in symbolic and absolute modes. Symbolic deals with symbols such as rwx, whereas absolute deals with octal values. For each of the three sets of permission on a fileread, write, and executeread is assigned the number 4, write is assigned the number 2, and execute is assigned the number 1. To make sure that permissions are wide open for yourself, the group, and all users, the command would be chmod 777 demofile.
Access for users and system processes are assigned a User ID (UID) and a Group ID (GID). Groups are the logical grouping of users that have similar requirements. This information is contained in the /etc/passwd file. An example is listed below
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:
daemon:x:2:2:daemon:/sbin:
adm:x:3:4:adm:/var/adm:
lp:x:4:7:lp:/var/spool/lpd:
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:
news:x:9:13:news:/var/spool/news:
operator:x:11:0:operator:/root:
gopher:x:13:30:gopher:/usr/lib/gopher-data:
ftp:x:14:50:FTP User:/home/ftp:
xfs:x:43:43:X Font Server:/etc/X11/fs:/bin/false
named:x:25:25:Named:/var/named:/bin/false
abc:x:503:503:Mike:/home/mg:/bin/bash
You will notice that root is the first account in the list. Root is always assigned the UID 0 and the GID 0. Other special users and accounts associated with services and daemons are listed after root and have values below 100. Red Hat starts regular users at a UID of 500. The fields are denoted by the colons.
- The username is the first field. Initial capitalization is not used to avoid upper/lowercase confusion.
- The second field holds the encrypted password. The field is marked by an x in this case; that is because this particular Linux system is using shadow passwords, which are held in /etc/shadow. The shadow file is used to increase security and is located at /etc/shadow. The third field is the UID. ABC’s UID is 503 and any file abc owns or creates will have this number associated with it.
- The fourth field is the GID. ABC’s GID is 503. The GID and UID are the same.
- The fifth field is the user description. This field holds descriptive information about the user. It can sometimes contain phone numbers, mail stops, or some other contact information. This is not a good idea as it can be reported by the finger utility.
- The sixth field is the User’s Home Directory. When the user is authenticated, the login program uses this field to define the user’s $HOME variable. By default, in all Linux distributions, the user’s home directory will be assumed to be /home/username.
- The seventh and final field is the User’s Login Shell. When the user is authenticated, the login program also sets the users $SHELL variable to this field. By default, in all Linux distributions, a new user’s login shell will be set to /bin/bash, the Bourne Again Shell.
Adding users to Linux is done by the useradd command. Files such as passwd are world readable, the shadow file is only readable by root. If an attacker can gain access to the root account, he has essentially taken control of the computer from you. For this reason, the root account must be protected at the highest level. The Substitute User (SU) command will allow to perform duties as a different user than the one you are logged in as. The command is simply su <username>.
Passwords and the Shadow File
Linux requires that user accounts have a password, but by default, it will not prevent user from leaving one set as blank. During installation, Linux gives the user the choice of setting the password encryption standard. Most versions of Linux, such as Red Hat, use MD5 by default. If you choose not to use MD5, you can choose DES, although it limits passwords to eight alphanumeric characters. Linux also includes the /etc/shadow file for additional password security. An sample entry from an /etc/shadow file is
root:$1$Gjt/eO.e$pKFFRe9QRb4NLvSrJodFy.:0:0:root:/root:/bin/bash
Moving the passwords to the shadow makes it less likely that the encrypted password can be decrypted because only the root user has access to the shadow file. The format of the password file is formatted as follows:
Account_name:Password:Last:Min:Max:Warn:Expire:Disable:Reserved
If logged in a root and would like to see the shadow passwords on your computer, use the following command – more /etc/shadow
Passwords in Linux systems use salts, which are needed to add a layer of randomness to the passwords. Because MD5 is a hashing algorithm, this means that if I used “secret” for my password and another user used “secret” for his password, encrypted values would look the same. A salt can be one of 4,096 values and helps further scramble the password. Under Linux, the MD5 password is 32 characters long and begins with $1$. The characters between the second and third $ represent the salt. In the previous example, that value is Gjt/eO.e. Passwords created in this way are considered to be one way. That is, there is no easy way to reverse the process.
The shadow file isn’t the only way to help guard against attackers who try to bypass the authentication process. There are other more advanced ways to protect resources. Passwords are one of the weakest forms of authentication. There is also something you have (tokens) and something you are (biometrics). If a new authentication scheme is going to be used, there needs to be a way to alert applications to this fact without having to rewrite every piece of code already developed. Pluggable Authentication Modules (PAM) enables a program designed to forgo the worry of the types of authentication that will be performed and concentrate on the application itself. PAM is used by FreeBSD, Linux, Solaris, and others. Its role is to control interaction between the user and authentication. This might be telnet, FTP, logging in to the console, or changing a password. PAM supports stronger authentication schemes, such as Kerberos, S/Key, and RADIUS. The directory that holds the modules specific to PAM is in /etc/pam.d/.
Services and rhosts file
A Linux service is an application (or set of applications) that runs in the background waiting to be used, or carrying out essential tasks. I’ve already mentioned a couple of typical ones (Apache and MySQL). If you look in the file /etc/inittab you will see something like:
id:4:initdefault:l
0:0:wait:/etc/rc.d/rc.0l
6:6:wait:/etc/rc.d/rc.6x
1:4:wait:/etc/rc.d/rc.4
The boot process uses these parameters to identify the default runlevel and the files that will be used by that runlevel. In this example, runlevel 4 is the default and the scripts that define runlevel 4 can be found in /etc/rc.d/rc.4.
Runlevel refers to different levels that the system goes through during a boot up. Instead, think of the runlevel as the point at which the system is entered. Runlevel 1 is the most basic configuration (simple single user access using an text interface), while runlevel 5 is the most advanced (multi-user, networking, and a GUI front end). Runlevels 0 and 6 are used for halting and rebooting the system.
There are, however, differences between Linux distributions. For instance, Fedora uses runlevel 5 for X-based logins, whereas Slackware uses runlevel 4 to do the same job. Therefore, you should check your documentation before making any changes. This table shows a generic list of configurations
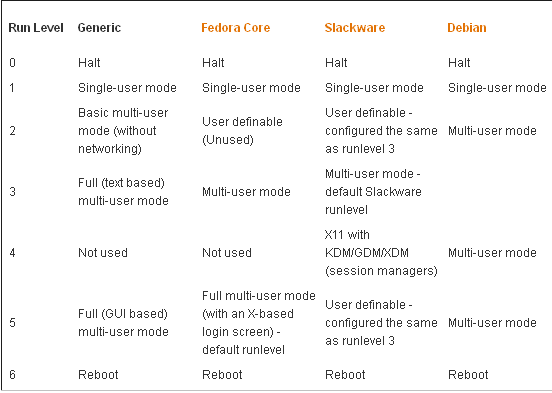
There are slight (but important) differences between Linux distributions. One thing is common between them — if you want to change the default level, you must edit /etc/initab. You will need to be root or use sudo to edit this file. Runlevels 0 and 6 should never be used as a default (for obvious reasons — you don’t want the system to shutdown or reboot as soon as you turn it on). You can, of course, change mode whilst the system is running. Type init followed by the required runlevel e.g.
init 6
This will reboot the system. The init command, will decide the runlevel to select and from that will decide the rc.d script files to be run. In this case either the file /etc/rc.d/rc.4 or any files in the directory /etc/rc.d/rc4.d. Let’s look at an example rc.d script file. Here’s the default rc.4 file for Slackware 10.2:
# Try to use GNOME’s gdm session manager:
if [ -x /usr/bin/gdm ];
then exec /usr/bin/gdm -nodaemonfi
# Not there? OK, try to use KDE’s KDM session manager:
if [ -x /opt/kde/bin/kdm ];
then exec /opt/kde/bin/kdm -nodaemonfi
# If all you have is XDM, I guess it will have to do:
if [ -x /usr/X11R6/bin/xdm ];
then exec /usr/X11R6/bin/xdm -nodaemonfi
As you would expect, since runlevel 4 is the Slackware X11 mode, the commands are all concerned with the setting up of the graphical interface. In the other distros (such as Fedora and Debian) you’ll find that the scripts to be run are actually symbolic links to files in the directory /etc/init.d — the central repository for all startup scripts. So all you have to do is to write your startup script, place it in /etc/init.d, and then create a symbolic link to it from the appropriate runlevel directory (or runlevel file, if that’s what your system uses).
For example, runlevel 2 is the default runlevel for Debian in non-GUI mode. If you’re running Apache 2 on Debian, you’d find an init script for Apache 2 under /etc/init.d called apache2. A symlink, S91apache2, points to /etc/init.d/apache2 from /etc/rc2.d — this tells init to start Apache 2 in runlevel 2, but only after other services with lower S numbers.
When the system is shut down, there is another symlink in the /etc/rc0.d and /etc/rc6.d directories (halt and reboot, respectively) that starts with a K instead of an S, which tells init to shut down the process. Instead simply make use of the /etc/rc.d/rc.local file. This script file is run once, before all other scripts have run but before the logon prompt appears. By default it looks something like:
#!/bin/bash## /etc/rc.local – run once at boot time
# Put any local setup commands in here:
You can append your instructions onto the end of the file by defining another script to be run:
/root/bin/start_bb

