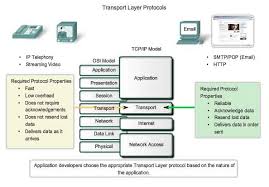
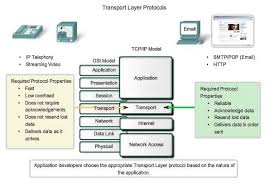
Elements Of Transport Protocols
Following are some of the elements of transport protocol-
- Addressing:
- At the transport layer , a transport layer address called a port number is required to choose among multiple processes running on the destination host.
- The destination port number is required for delivery and the source port number is needed for the reply.
- In the internet model , the port numbers are 16 bit integers between 0 and 65,535. This number is called as ephemeral port number.
- The server process should define itself with a port number but this number cannot be chosen randomly. The internet uses universal port numbers for servers and these port numbers are called as well known port numbers.
- Every client process knows the well known port number of the corresponding server process.
- The IP address and port numbers play different roles in selecting the final destination of data. The destination IP address defines the host among the millions of hosts in the world. After a particular host is selected, the port number defines one of the processes on this selected host.
2. Connection Establishment:
- Let’s assume that host A sends a connection request packet to B. This includes the initialization information about traffic from A to B.
- Host B sends the packet of acknowledgement to confirm that it has received the request from A.
- Host B sends a connection request to A along with the initialization information about traffic from B to A.
- Host A sends a packet of acknowledgement to confirm the request of B.
- Thus these are the steps involved in connection establishment.
- PROBLEMS:
1. Due to congestion on a subnet , the acknowledgements do not get back in time. So retransmission of each packet takes place.
2. If the subnet uses datagrams inside and every packet travels on a different route. Some of the packets might get stuck in a traffic jam and take a long time to arrive.
- REMEDY:
The solution to these problems is to kill off the aged packets that are still wandering about . The packet lifetime can be restricted by using one of the following techniques:
1. Restricted subnet design. 2. Putting a hop counter in each packet. 3. Time stamping each packet.
3. Connection Release:
- Any one if the two parties involved in data exchange can close the connection. But the problem is that, when connection is terminated from one end,the other party can continue to send data in the other direction. Hence, to ensure a proper connection release one has to follow the following steps:
- Host 1 sends a connection release request to host 2.
- Host 2 sends an acknowledgment to confirm the request of host 1.
- After this, the connection is closed in one direction but host 2 can continue to send data to host 1.
- When host 2 finishes sending data , it sends a connection release request to host 1.
- Host 1 acknowledges the request made by host 2 and the connection is released from both ends.
- Thus releasing a connection is easy than establishing it.
Click here for government certification in Information Technology



6 Comments. Leave new
Never given this a thought,very informative, indeed a great job, great effort s
Good job 🙂
nice series
Nice,, enjoyed reading !
That’s a worth read!
Great work!