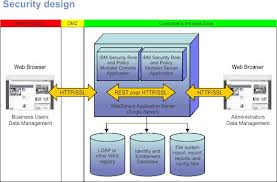
Security Design and authentication
web application has more than one class of users, the you’re going to need some sort of authentication system. On the web, authentication systems have to constantly carry “tokens” around, submitting them to the server at every request. This is a downside to the stateless HTTP model – infact, with web based applications, you’ll spend alot of time creating the illusion of a stateful environment through the use of authentication and location tokens.
When designing your own authentication system, there are a few things you’ll need to decide upon. The first question you should be asking yourself is if you really need to write your own. An insecure authentication system can leave your application data and even your server copen to attackers. If you decide you really do need to write your own system, then read through the following checklist first.
1. Elements
2. Storage
3. HTTPS
4. Token Passing
5. Sessions
6. Conclusion
Apply for Software Security Professional Certification Now!!
https://www.vskills.in/certification/certified-software-security-professional