File Transfer Protocol (FTP) is a network protocol to transfer files from one host or to another host over a TCP-based network, such as the Internet. It is a client-server architecture and using separate control and data connections between the client and the server. Authentication is in clear-text username and password, and if allowed on server, anonymous access can also be done. Secure transmission with traffic encryption uses SSL/TLS and called SSH FTP or SFTP.
FTP was specified in June 1980 and updated in RFC 959. FTP server responds over the control connection with three-digit status codes in ASCII with an optional text message like 200 or “200 OK” for successful last command. FTP process between Client “A” and server “S” is shown
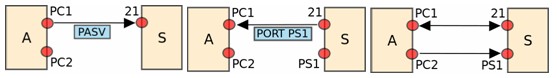
Both the client and server have two processes allowing these two types of information to be managed
- DTP (Data Transfer Process) is the process in charge of establishing the connection and managing the data channel. The server side DTP is called SERVER-DTP, the client side DTP is called USER-DTP
- PI (Protocol Interpreter) interprets the protocol allowing the DTP to be controlled using commands received over the control channel. It is different on the client and the server
- The SERVER-PI is responsible for listening to the commands coming from a USER-PI over the control channel on a data port, establishing the connection for the control channel, receiving FTP commands from the USER-PI over this, responding to them and running the SERVER-DTP.
- The USER-PI is responsible for establishing the connection with the FTP server, sending FTP commands, receiving responses from the SERVER-PI and controlling the USER-DTP if needed.
When an FTP client is connected to a FTP server, the USER-PI initiates the connection to the server according to the Telnet protocol. The client sends FTP commands to the server, the server interprets them, runs its DTP, then sends a standard response. Once the connection is established, the server-PI gives the port on which data will be sent to the Client DTP. The client DTP then listens on the specified port for data coming from the server.
FTP may be in active or passive mode. In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client’s specified data port from its local data port, which is port 20. In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1023) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data. While transferring data over the network, four data representations can be used ASCII mode (for text in 8-bit ASCII), image or binary mode (sends data as bytestream), EBCDIC mode (for text using the EBCDIC character set) and local mode (end nodes send data in a proprietary format).
Data transfer is done in three modes of stream (data is sent as a continuous stream and no EOF needed) , block mode (data broken into blocks like block header, byte count and data field) and compressed mode ( data is compressed by run-length encoding).
Secure File Transfer Protocol (SFTP)
SFTP is a network protocol to provide FTP data transfer over reliable data connection. SFTP uses SSH to provide encrypted connection over the SSH port 22. SFTP connection encrypts commands and data channels to prevent password and sensitive information from being transmitted insecurely over the network. Except for the method of connecting, SFTP functioning is similar to FTP. An SFTP-enabled FTP client and server are needed for implementing SFTP.
FTP Modes
When an FTP client application initiates a connection to an FTP server, it opens port 21 on the server — known as the command port. This port is used to issue all commands to the server. Any data requested from the server is returned to the client via a data port. The port number for data connections, and the way in which data connections are initialized, vary depending upon whether the client requests the data in active or passive mode. The following defines these modes
- active mode – Active mode is the original method used by the FTP protocol for transferring data to the client application. When an active mode data transfer is initiated by the FTP client, the server opens a connection from port 20 on the server to the IP address and a random, unprivileged port (greater than 1024) specified by the client. This arrangement means that the client machine must be allowed to accept connections over any port above 1024. With the growth of insecure networks, such as the Internet, the use of firewalls to protect client machines is now prevalent. Because these client-side firewalls often deny incoming connections from active mode FTP servers, passive mode was devised.
- passive mode – Passive mode, like active mode, is initiated by the FTP client application. When requesting data from the server, the FTP client indicates it wants to access the data in passive mode and the server provides the IP address and a random, unprivileged port (greater than 1024) on the server. The client then connects to that port on the server to download the requested information. While passive mode resolves issues for client-side firewall interference with data connections, it can complicate administration of the server-side firewall. You can reduce the number of open ports on a server by limiting the range of unprivileged ports on the FTP server. This also simplifies the process of configuring firewall rules for the server.
vsftpd
The Very Secure FTP Daemon (vsftpd) is designed from the ground up to be fast, stable, and, most importantly, secure. vsftpd is the only stand-alone FTP server distributed with Fedora, due to its ability to handle large numbers of connections efficiently and securely.
The vsftpd RPM installs the daemon (/usr/sbin/vsftpd), its configuration and related files, as well as FTP directories onto the system. The following lists the files and directories related to vsftpd configuration
- /etc/rc.d/init.d/vsftpd — The initialization script (initscript) used by the systemctl command to start, stop, or reload vsftpd.
- /etc/pam.d/vsftpd — The Pluggable Authentication Modules (PAM) configuration file for vsftpd. This file specifies the requirements a user must meet to login to the FTP server.
- /etc/vsftpd/vsftpd.conf — The configuration file for vsftpd.
- /etc/vsftpd/ftpusers — A list of users not allowed to log into vsftpd. By default, this list includes the root, bin, and daemon users, among others.
- /etc/vsftpd/user_list — This file can be configured to either deny or allow access to the users listed, depending on whether the userlist_deny directive is set to YES (default) or NO in /etc/vsftpd/vsftpd.conf. If /etc/vsftpd/user_list is used to grant access to users, the usernames listed must not appear in /etc/vsftpd/ftpusers.
- /var/ftp/ — The directory containing files served by vsftpd. It also contains the /var/ftp/pub/ directory for anonymous users. Both directories are world-readable, but writable only by the root user.
Although vsftpd may not offer the level of customization other widely available FTP servers have, it offers enough options to fill most administrator’s needs. The fact that it is not overly feature-laden limits configuration and programmatic errors.
All configuration of vsftpd is handled by its configuration file, /etc/vsftpd/vsftpd.conf. Each directive is on its own line within the file and follows the following format
directive=value
For each directive, replace directive with a valid directive and value with a valid value. The following is a list of directives which control the overall behavior of the vsftpd daemon.
- listen — When enabled, vsftpd runs in stand-alone mode. Red Hat Enterprise Linux sets this value to YES. This directive cannot be used in conjunction with the listen_ipv6 directive. The default value is NO.
- listen_ipv6 — When enabled, vsftpd runs in stand-alone mode, but listens only to IPv6 sockets. This directive cannot be used in conjunction with the listen directive. The default value is NO.
- session_support — When enabled, vsftpd attempts to maintain login sessions for each user through Pluggable Authentication Modules (PAM).
The following is a list of directives which control the login behavior and access control mechanisms.
- anonymous_enable — When enabled, anonymous users are allowed to log in. The usernames anonymous and ftp are accepted. The default value is YES.
- banned_email_file — If the deny_email_enable directive is set to YES, this directive specifies the file containing a list of anonymous email passwords which are not permitted access to the server. The default value is /etc/vsftpd.banned_emails.
- banner_file — Specifies the file containing text displayed when a connection is established to the server. This option overrides any text specified in the ftpd_banner directive. There is no default value for this directive.
- cmds_allowed — Specifies a comma-delimited list of FTP commands allowed by the server. All other commands are rejected. There is no default value for this directive.
- deny_email_enable — When enabled, any anonymous user utilizing email passwords specified in the /etc/vsftpd.banned_emails are denied access to the server. The name of the file referenced by this directive can be specified using the banned_email_file directive. The default value is NO.
- ftpd_banner — When enabled, the string specified within this directive is displayed when a connection is established to the server. This option can be overridden by the banner_file directive. By default vsftpd displays its standard banner.
- local_enable — When enabled, local users are allowed to log into the system. The default value is YES.
- pam_service_name — Specifies the PAM service name for vsftpd. The default value is ftp. The default value is NO.
- userlist_deny — When used in conjunction with the userlist_enable directive and set to NO, all local users are denied access unless the username is listed in the file specified by the userlist_file directive. Because access is denied before the client is asked for a password, setting this directive to NO prevents local users from submitting unencrypted passwords over the network. The default value is YES.
- userlist_enable — When enabled, the users listed in the file specified by the userlist_file directive are denied access. Because access is denied before the client is asked for a password, users are prevented from submitting unencrypted passwords over the network. The default value is NO, however under Red Hat Enterprise Linux the value is set to YES.
- userlist_file — Specifies the file referenced by vsftpd when the userlist_enable directive is enabled. The default value is /etc/vsftpd.user_list and is created during installation.
- cmds_allowed — Specifies a comma separated list of FTP commands that the server allows. Any other commands are rejected. There is no default value for this directive.
The following lists directives which control anonymous user access to the server. To use these options, the anonymous_enable directive must be set to YES.
- anon_mkdir_write_enable — When enabled in conjunction with the write_enable directive, anonymous users are allowed to create new directories within a parent directory which has write permissions. The default value is NO.
- anon_root — Specifies the directory vsftpd changes to after an anonymous user logs in. There is no default value for this directive.
- anon_upload_enable — When enabled in conjunction with the write_enable directive, anonymous users are allowed to upload files within a parent directory which has write permissions. The default value is NO.
- ftp_username — Specifies the local user account (listed in /etc/passwd) used for the anonymous FTP user. The home directory specified in /etc/passwd for the user is the root directory of the anonymous FTP user. The default value is ftp.
- no_anon_password — When enabled, the anonymous user is not asked for a password. The default value is NO.
Apply for Linux Administration Certification Now!!
http://www.vskills.in/certification/Certified-Linux-Administrator

