A network is a collection of computers and other hardware components interconnected by communication channels that allow sharing of resources and information.
Networking is the practice of linking two or more computing devices together for the purpose of sharing data. Networks are built with a mix of computer hardware and computer software. A host device on a network can be computers, servers, laptops, Personal Digital Assistants (PDAs), or anything a person uses to access the network. Network devices are hubs, repeaters, bridges, switches, router and firewall.
Layered Network Model
The layered network model defines a networking framework for implementing protocols in different layers. Control is passed from one layer to the next, starting at the top most layer in one station, proceeding to the bottom layer, over the channel to the next station and back up the hierarchy.
The International Standards Organization (ISO) defined a seven-layer model to standardize networking processes. The benefits to layering networking protocol specifications are many including
- Interoperability – Greater interoperability between devices from different manufacturers and between different generations of same type of device from the same manufacturer.
- Compatibility – Compatibility between devices, systems and networks that this delivers.
- Better Flexibility – Improved flexibility in options and choices for configuration and installation.
- Increased Life Expectancy – Devices from different technology generations can co-exist thus the older units do not get discarded immediately newer technologies are adopted.
- Scalability – Experience shows that a layered design scales better than the horizontal approach.
- Value Added Features – It is easier to add and implement value added features into products or services when the entire system has been built on the use of a layered philosophy.
- Modularity Plug-ins and add-ons are easily added from use of a layered approach.
- Standardization and Certification –The layered design specifications facilitate streamlined and simple standardization and certification process due to the clearer and more distinct definition.
- Portability – Layered networking protocols are much easier to port from one system to another.
- Compartmentalization of Functionality – It gives freedom to concentrate on a specific layer or specific functions without the need for concern or modification of any other layer.
TCP/IP Protocol Architecture
TCP/IP provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination. The TCP/IP model and related protocols are maintained by the (IETF) or Internet Engineering Task Force. The Internet protocol suite and the layered protocol stack design were in use before the OSI model was established. It has four abstraction layers, each with its own protocols. It has four abstraction layers, each with its own protocols. From highest to lowest, the layers are
- Application layer (process-to-process)– It contains all protocols (like HTTP) for specific data communications services on a process-to-process level (for example how a web browser communicates with a web server). This is the scope within which applications create user data and communicate this data to other processes or applications on another or the same host. The communications partners are often called peers. This is where the “higher level” protocols such as SMTP, FTP, SSH, HTTP, etc. operate.
- Transport layer (host-to-host)- It handles host-to-host communication. The transport layer constitutes the networking regime between two network hosts, either on the local network or on remote networks separated by routers. The transport layer provides a uniform networking interface that hides the actual topology (layout) of the underlying network connections. This is where flow-control, error-correction, and connection protocols exist, such as TCP. This layer deals with opening and maintaining connections between Internet hosts.
- Internet layer (internetworking)- It connects local networks, thus establishing internetworking. The internet layer has the task of exchanging datagrams across network boundaries. It is therefore also referred to as the layer that establishes internetworking, indeed, it defines and establishes the Internet. This layer defines the addressing and routing structures used for the TCP/IP protocol suite. The primary protocol in this scope is the Internet Protocol, which defines IP addresses. Its function in routing is to transport datagrams to the next IP router that has the connectivity to a network closer to the final data destination.
- Link layer- The link layer (commonly Ethernet) contains communication technologies for a local network. This layer defines the networking methods within the scope of the local network link on which hosts communicate without intervening routers. This layer describes the protocols used to describe the local network topology and the interfaces needed to affect transmission of Internet layer datagrams to next-neighbor hosts.
Application, Transport, Internet and Network Access Layer
Application Layer
It contains all protocols and methods of process-to-process communications across an Internet Protocol (IP) network. Its methods use the underlying transport layer protocols to establish host-to-host connections. Both TCP/IP and the OSI model specify a group of protocols and methods identified by the name application layer. The following protocols are described in the application layer of the Internet protocol suite.
- Remote login – Telnet
- File transfer – FTP, TFTP
- Electronic mail – SMTP,IMAP, POP
- Support services – DNS, RARP, BOOTP, SNMP
Transport Layer
The transport layer or layer 4 provides end-to-end communication services for applications by providing services like connection-oriented data stream support, reliability, flow control, and multiplexing. It is contained in the TCP/IP as TCP and in the OSI model as transport layer.
The Transmission Control Protocol (TCP) is used for connection-oriented transmissions, whereas the connectionless User Datagram Protocol (UDP) is used for simpler messaging transmissions. TCP has stateful design for reliable transmission and data stream services. Various services provided by a transport-layer protocol include
- Connection-oriented communication- Interpreting the connection as a data stream provides benefits to applications.
- Byte orientation- It is easier to process data stream as a sequence of bytes helping various underlying message formats.
- Same order delivery- The network layer doesn’t guarantee data packet arrival in the same order that they were sent, hence segment numbering is used, with the receiver passing them to the application in order.
- Reliability- Packets may be lost due to network congestion hence, an error detection code like checksum checks data corruption, and verify correct receipt by sending an ACK or NACK message to sender. Automatic repeat request retransmits lost or corrupted data.
- Flow control- The rate of data transmission between two nodes is managed to prevent a fast sender for more data. It also improves efficiency by reducing buffer under run.
- Congestion avoidance- It controls traffic entry into a network by avoiding oversubscription of link capabilities of intermediate nodes and networks by reducing rate of sending packets.
- Multiplexing- Ports provide multiple endpoints on a single PC like the name on a postal address is a multiplexing, and differs between different recipients at same location. Computer applications each listen for information on their own ports, which enables the use of more than one network service at the same time.
Internet Layer or IP Layer
It is a group of internetworking methods, protocols, and specifications used to transport datagrams (packets) from the originating host across network, to destination host specified by a network address (IP address). It facilitates internetworking or connecting multiple networks by gateways.
Internet-layer protocols use IP-based packets and have three functions, for outgoing packets, select the next-hop host (gateway) and transmit the packet to this host by passing it to the appropriate link layer implementation; for incoming packets, capture packets and pass the packet payload up to the appropriate transport-layer protocol, if appropriate. In addition it provides error detection and diagnostic capability. The Version 4 of the IP (IPv4), IP is capable of automatic fragmentation or de-fragmentation of packets, based on the maximum transmission unit (MTU) of link elements.
It is not responsible for reliable transmission and offers “best effort” delivery hence, no proper arrival making network resilient and assigning reliability provision to higher level protocols. In IPv4 (not IPv6), a checksum is used to protect the header of each datagram.
Network Access Layer
It is the lowest layer which provides the means for the system to deliver data to the other devices on a directly attached network. It defines how to use the network to transmit data and thus, must know the details of the underlying network to correctly format the data being transmitted to comply with the network constraints. The TCP/IP Network Access Layer has the functions of all three lower layers of OSI (Network, Data Link, and Physical).
Functions performed at this level include encapsulation of IP datagrams into the frames transmitted by the network, and mapping of IP addresses to the physical addresses used by the network. One of TCP/IP’s strengths is its universal addressing scheme. The IP address must be converted into an address appropriate for physical network over which the datagram is transmitted.
Devices at different layers
Devices at different layers of TCP/P network model are
- Layer 1- It is the physical layer. Media converters operate at Layer 1 to convert electrical signals and physical media without doing anything to data coming through the link. Media converters have two ports—one in, one out— to convert the incoming electrical signal from one cable type and then transmit it over another type.
- Layer 2- It is the data-link layer. Switch and media converter operate at Layer 2 to sort packets using physical network addresses or MAC addresses. All network hardware is permanently assigned this number during its manufacture. Both switches and media converters can be Layer 2 devices. A switch has more ports than a media converter. Devices are fast, but aren’t smart as they don’t look at data packets closely.
- Layer 3- It is the Network Layer and layer 3 switches use network or IP addresses to identify locations on the network. Layer 3 switches are smarter due to routing functions to find the best way to send a packet to its destination.
- Network Router – A router routes data packets between two networks by reading the destination information in each packet so, for an immediate network it has access to, it will strip the outer packet, readdress the packet to the proper Ethernet address, and transmit it but, for another network destination it is sent to another router, re-package outer packet to receive by next router and send it to next router.
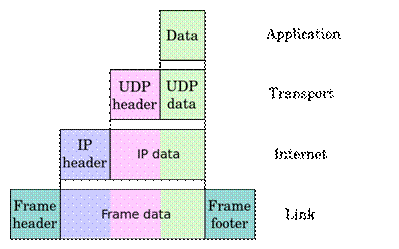
Data Encapsulation
It is a method for communication protocols to logically separate functions in the network and abstracts it from their underlying structures by inclusion or information hiding within higher level objects. Link encapsulation by the physical layer allows local area networking by higher layers and IP provides global addressing of individual computers; UDP adds application or process selection, i.e., the port specifies the service such as a Web or TFTP server.
The more abstract layer is called the upper layer protocol while the more specific layer is called the lower layer protocol. Encapsulation is a characteristic feature of most networking models, including the OSI Model and TCP/IP suite of protocols. An image of encapsulation of application data descending through the layers
The OSI Reference Model
The OSI or Open System Interconnection reference model defines a networking framework for implementing protocols in seven layers. Control is passed from one layer to the next, starting at application layer in source and to bottom layer, over channel to destination and back up hierarchy.
Application (Layer 7)
It supports application and end-user processes. Communication destination is identified, quality of service found, user authentication and privacy are considered and any constraints on data syntax are identified. Everything at this layer is application-specific. This layer provides application services for file transfers, e-mail, and other network software services. Telnet and FTP are applications that exist entirely in the application level.
Presentation (Layer 6)
It provides independence from differences in data representation (e.g., encryption) by translating
from application to network format, and vice versa. It transforms data into the form that the application layer can accept by formatting and encrypting data to be sent across a network so, providing freedom from compatibility problems. It is also called the syntax layer.
Session (Layer 5)
It establishes, manages and terminates connections between applications. It sets up, coordinates,
and terminates conversations, exchanges, and dialogues between the applications at each end. It deals with session and connection coordination.
Transport (Layer 4)
It provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. It ensures complete data transfer.
Network (Layer 3)
It provides switching and routing technique, creates logical paths called virtual circuits to transmit data from node to node. Routing and forwarding are functions of this layer, as well as addressing, internetworking, error handling, congestion control and packet sequencing.
Data Link (Layer 2)
In it data packets are encoded and decoded into bits. It handles errors in the physical layer, flow control and frame synchronization. It is divided into two sub layers of Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. The MAC sub layer controls how a computer on the network gains access to the data and permission to transmit it. The LLC layer controls frame synchronization, flow control and error checking.
Physical (Layer 1)
It transmits the bit stream – electrical impulse, light or radio signal — through the network at the electrical and mechanical level. It provides the hardware means of sending and receiving data on a carrier, including defining cables, cards and physical aspects. Fast Ethernet, RS232, and ATM are protocols with physical layer components.
OSI Layers and Their Functions
Physical Layer
It is the lowest layer of the OSI model and is concerned with the transmission and reception of the unstructured raw bit stream over a physical medium. It describes the electrical/optical, mechanical, and functional interfaces to physical medium, and carries signals for all higher layers. It provides
- Data encoding – modifies digital signal (1s and 0s) of PC to characteristics of physical medium, and to aid in bit and frame synchronization like signal state for a binary 1, “bit-time” starts, etc.
- Transmission technique – determines whether the encoded bits will be transmitted by base band (digital) or broadband (analog) signaling.
- Physical medium transmission – transmits bits as electrical or optical signals appropriate for the physical medium.
Data Link Layer
It gives error-free data frames transfer from one node to another over the physical layer, allowing top layers an error-free transmission over the link. The data link layer provides
- Link establishment and termination – establishes and terminates logical link between two nodes.
- Frame traffic control – tells sender to “back-off” when no frame buffers are available.
- Frame sequencing – transmits/receives frames sequentially.
- Frame acknowledgment – provides/expects frame acknowledgments. Detects and recovers from physical layer errors by retransmitting non-acknowledged frames and handling duplicate frame receipt.
- Frame delimiting – creates and recognizes frame boundaries.
- Frame error checking – checks received frames for integrity.
- Media access management – determines when the node “has the right” to use the physical medium.
Network Layer
It controls the operation of the subnet, deciding which physical path the data should take based on network conditions, priority of service, and other factors. It provides
- Routing – routes frames among networks.
- Subnet traffic control – routers (network layer intermediate systems) can instruct a sending station to “throttle back” its frame transmission when the router’s buffer fills up.
- Frame fragmentation – if it determines that a downstream router’s maximum transmission unit (MTU) size is less than the frame size, a router can fragment a frame for transmission and re-assembly at the destination station.
- Logical-physical address mapping – translates logical addresses, or names, into physical addresses.
- Subnet usage accounting – It has accounting functions to keep track of frames forwarded by subnet intermediate systems, to produce billing information.
This layer builds headers and uses them to route data to the destination address thus, relieving upper layers. It establishes, maintains and terminates connections across communications subnet.
Peer protocols also exist between a node and its immediate neighbor, but the neighbor may be a node through which data is routed, not the destination station.
Transport Layer
It ensures that messages are delivered error-free, in sequence, and with no losses or duplications. It relieves the higher layer protocols from concern of data transfer. In a reliable network layer with virtual circuit capability, a minimal transport layer is required but, unreliable one only supporting datagrams, the transport protocol should include extensive error detection and recovery. The transport layer provides
- Message segmentation – splits received message into smaller units, and passes down to the network layer. The transport layer at the destination station reassembles the message.
- Message acknowledgment – provides reliable end-to-end message delivery with acknowledgments.
- Message traffic control – tells the source to “back-off” when no message buffers are available.
- Session multiplexing – multiplexes several message streams, or sessions onto one logical link.
There are strict message size limits imposed by the network (or lower) layer so, the transport layer must break up the messages into smaller units, or frames, with a header to each frame.
The transport layer header information must then include control information, such as message start and message end flags, to enable the transport layer on the other end to recognize message boundaries.
The transport layer and the layers above are true “source to destination” or end-to-end layers, and are not concerned with the details of the underlying communications facility. Transport layer software (and software above it) on the source carries on a conversation with similar software on the destination by using message headers and control messages.
Session Layer
It allows session establishment between processes running on different nodes. It provides
- Session establishment, maintenance and termination – allows two application processes on different machines to establish, use and terminate a connection, called a session.
- Session support – performs the functions that allow these processes to communicate over the network, performing security, name recognition, logging, and so on.
Presentation Layer
The presentation layer formats the data to be presented to the application layer. This layer may translate data from a format used by the application layer into a common format at the source then, translate the common format to a format known to application layer at destination. The presentation layer provides
- Character code translation – like, ASCII to EBCDIC.
- Data conversion – bit order, CR-CR/LF, integer-floating point, and so on.
- Data compression – reduces the number of bits that need to be transmitted on the network.
- Data encryption – encrypt data for security purposes. like, password encryption.
Application Layer
It serves as the window for users and application processes to access network services. This layer contains a variety of commonly needed functions
- Resource sharing and device redirection
- Remote file access
- Remote printer access
- Inter-process communication
- Network management
- Directory services
- Electronic messaging (such as mail)
- Network virtual terminals
Apply for IT Support Certification
https://www.vskills.in/certification/certified-it-support-professional

